I'm always excited to connect with professionals, collaborate on cybersecurity projects, or share insights.
I'm always excited to connect with professionals, collaborate on cybersecurity projects, or share insights.
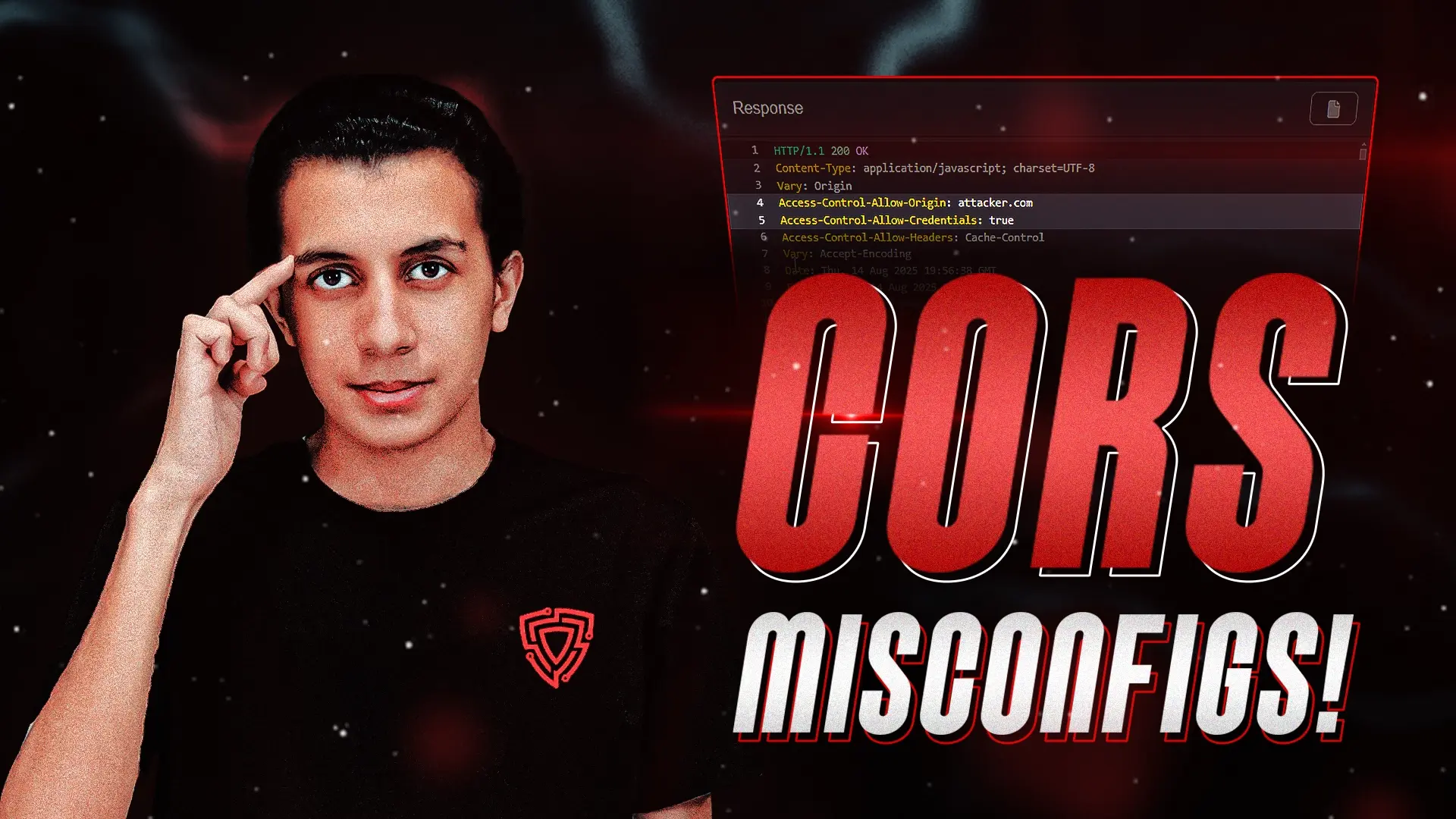
When I first started seeing CORS bugs, I thought… “Okay, cool, but this is probably nothing serious.”
Wrong.
In this breakdown, we’ll hit the 4 most dangerous CORS mistakes I keep finding, how to spot them fast, and why they can lead to account takeover, data leaks, and even complete system compromise.
Table of contents [Show]
When Access-Control-Allow-Origin is set to * and Access-Control-Allow-Credentials is true, you’ve basically given any origin full access to your authenticated data.
What to check:
The server takes whatever Origin you send… and reflects it back in the Access-Control-Allow-Origin header.
With Access-Control-Allow-Credentials: true, this becomes dangerous: your malicious site can make the request as the victim, and the browser will happily send their cookies.
What to check:
A lot of WP sites leave /wp-json/ open to the world with permissive CORS rules.
Why it’s bad:
Rails apps often use the rack-cors gem, and if it’s misconfigured, you can access internal or authenticated endpoints from anywhere.
What to check:
origins '*' with credentials: true.
The Real Hacker Mindset
Most hunters shrug at CORS — they see it as “informational” and move on.
But combine it with XSS, CSRF, or cache poisoning, and you’re looking at account takeover, password resets, or sensitive data exfiltration.
Final Words
The next time you see a “boring” CORS issue… stop. Test it. Chain it. Escalate it.
The boring bugs are often the ones with the biggest payouts.
Stay curious, and stay secure. 🔐🔥
Your email address will not be published. Required fields are marked *